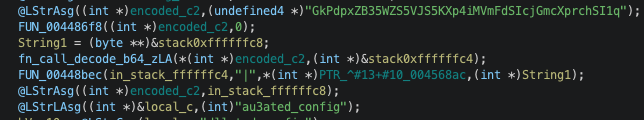
If you have ever analyzed a Delphi binary using Ghidra, you might have noticed the failure of the decompiler. As shown in the image below, the compiler tends to emit a lot of variables named like "stack0xffffffc4." This partially breaks the decompiler output and is not really readable at all.

All of this comes from the way Delphi binaries prepare the stack for local variables. The prologue of a function looks like this:
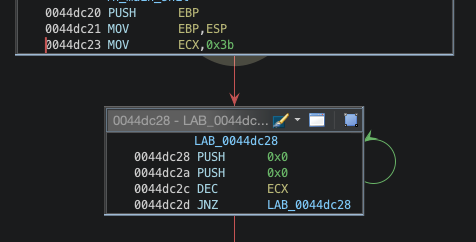
In this example, the program pushes 0x3b times two null DWORD on the stack. Replacing those instructions with a simple "sub esp, 0x1d8" (0x1d8 = (4 + 4) * 0x3b) is enough to clean the decompiler output:
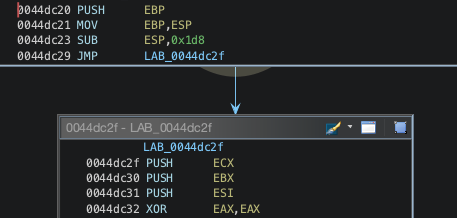
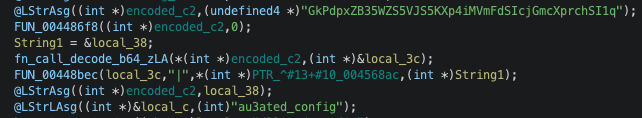
I did not develop the script that patch all functions' prologues, but it shouldn't be too complex.